Safeguard Your Assets. Maintain Customer Trust and Confidence.
Security is about detecting and responding in a timely, efficient, and effective manner. And it starts by understanding your current IT landscape. Security assessments from Zones Trusted Advisory Services can:
Measure control maturity
Identify vulnerabilities
Mitigate cyber risks
Help prevent costly breaches
Enhance incident response
Help maintain compliance
Increase team awareness and training
Enhance customer trust and loyalty
Unfortunately, cybercriminals are thriving. With advancements in technology and increasing digital dependency, cybercriminals have more opportunities to exploit vulnerabilities in networks, systems, and individuals.
News reports are now routine, covering the consequences of phishing and malware attacks, ransomware, and data breaches targeting valuable information and financial assets. And cybercriminals constantly adapt and evolve their tactics, making it an ongoing challenge to combat cyberthreats effectively.
As in other areas of your organization, understanding your strengths and weakness in cybersecurity is a must. It empowers you to go on the offensive. To put in place rigorous defenses to help stop cybercriminals in their tracks and minimize any damage they can do. You'll get that understanding from security assessments conducted by the experts at Zones.

"By identifying and addressing security risks early on, security assessments can help prevent costly security breaches and reduce the overall cost of maintaining security for your organization."
Security assessments enable a well-designed security improvement roadmap.
Our customer-centered approach begins with listening and collaboration. The Zones project team will team up with you to discuss your specific organizational cybersecurity needs and objectives. We'll then focus on the specification requirements for your Information Security Management System (ISMS). This information then forms the groundwork for the assessments that follow.
In turn, the valuable information, insights, and recommendations we provide enable the development of a well-designed security improvement roadmap.
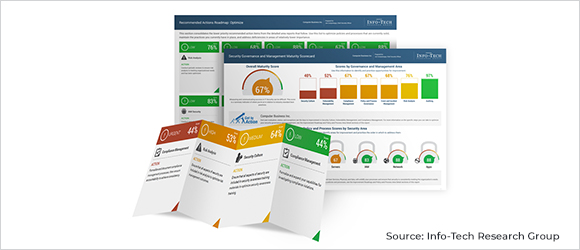
Security Governance and Management Scorecard Assessment
We'll assess your current operations based on best practices. The process includes an interactive workshop and survey to create a governance and management scorecard.
- Initial framework model is derived from two globally accepted frameworks we use to optimize the value of your IT: Control Objectives for Information and Related Technology (COBIT) and The Open Group Architecture Framework (TOGAF®).
- Identifies your current strengths and successes – useful information for year-over-year comparisons to build on your successes and measure long-term progress.
- Identifies areas for improvement and optimization – information you can use to justify the allocation of resources to achieve your security goals.
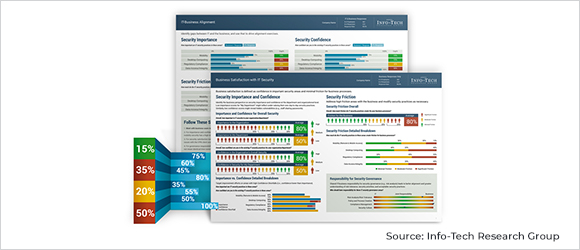
Security Business Satisfaction and Alignment Assessment
This assessment helps evaluate the effectiveness of your IT security measures and determine if they are aligned with your organization's goals and objectives. Specifically, this summary will:
- Measure the level of confidence in current security practices.
- Identify areas of friction for business users.
- Determine security importance from a business perspective.
This assessment will also identify gaps between IT and business perceptions of security practices. Specifically, this summary will:
- Measure gaps in perceptions of security confidence, importance, and satisfaction.
- Identify gaps in the desired level of business involvement in security governance.
- Provide recommended actions to close alignment gaps and optimize security practices.
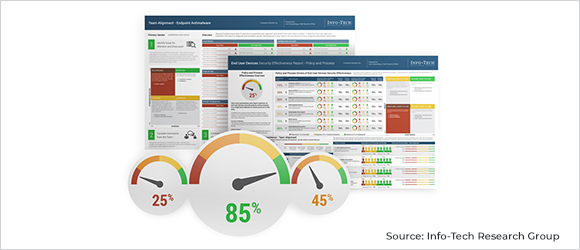
Security Process and Technology Effectiveness Assessments
These assessments aim to improve targeted IT security areas by analyzing your security processes and technology effectiveness. No one knows your organization's security processes and technologies better than your IT team.
Security effectiveness reports let you leverage the collective knowledge of your staff to enhance security effectiveness in the area (or areas) you'd like to focus on. We can use these reports to:
- Optimize policies and processes.
- Drive improvement in technology usage and decisions.
- Facilitate alignment, consistency, and knowledge transfer among your team.
Security effectiveness assessments are available in the following security areas:
- Governance and Management
- Network
- Servers
- End User Devices
- Data
- Applications
- Identity and Access Management
- Physical

Take a closer look at why security assessments are valuable tools for any organization.